How to Identify and Prevent Fraud on Your Personal and Business Accounts
Posted On: March 24, 2023 in: Security

The number of people falling victim to bank scams has continued to rise over the past few years and shows no signs of really slowing down. In 2021 alone, the FTC estimated that consumers lost 5.8 billion dollars to fraud, which was an increase of over 70% from 2020 numbers. The numbers are even more staggering for businesses, estimating that, globally, companies lose about 5% of their total revenue every year due to fraud. Here at Park Bank we want to make sure that you are well educated on what to look for, so that you don't become part of any of those statistics.
First, let's establish that fraud can happen to anyone. Victims tend to feel embarrassed and may not want to admit to the fact that they have fallen for a scam.
Common Scams
- Romance
- Also known as a confidence scam, this scam is when a fraudster tricks a victim into believing they are in a trusted relationship and uses that relationship to persuade them to give money, personal and/or financial information, or even items of value to the perpetrator.
- Grandparent
- Grandparent scams typically work something like this: The victim gets a call from someone posing as his or her grandchild. The fraudster explains, in a frantic-sounding voice, that he or she is in trouble (i.e., robbed, arrested, in an accident) and they need help. They persuade the grandparent to wire funds – as that is the only way to help them.
- Investment
- Investment fraud happens when people try to trick someone into investing money. These are bogus opportunities involving promises of big payouts, quick money, or guaranteed returns with little or no risk.
- Lottery
- A lottery scam is a type of advance-fee fraud which begins with an unexpected email notification, phone call, or mailing explaining, “You have won!” To claim the prize, the victim will be asked to pay a fee to cover insurance, government taxes, bank fees, or courier charges.
- Facebook Phishing
- Facebook phishing scams are very common right now. These messages claim that the recipient’s Facebook account has been hacked, stolen, or disabled, and urge them to click a link to recover their account. If the link is opened, users are asked to “log in” to a website that looks a lot like Facebook, but instead is a convincing fake set up by scammers to steal account information.
- Users concerned that their account may be compromised can seek help at facebook.com/hacked.
- If you are unsure of an email’s legitimacy, you should check the sender’s address to make sure it is from an office Facebook account. You can also hover over links in the email message without clicking or opening them to see where they lead.
Red Flags
- A seemingly legitimate emailed transaction instructions contain different language, timing, and amounts than previously verified, authentic transaction instructions.
- Transaction instructions originate from an email account closely resembling a known customer’s email account; however, the email address has been slightly altered by adding, changing, or deleting one or more characters.
- A message uses a name that closely resembles that of a better-known, reputable organization.
- A message uses high-pressure tactics like trying to get someone to donate immediately, without giving them time to think about it and do their research.
- Guaranteed sweepstakes winnings in exchange for a contribution. By law, you never have to give a donation to be eligible to win a sweepstakes.
- The person quickly wants to leave the dating website and communicate through email or instant messaging.
- He or she lavishes the target with attention. Swindlers often inundate prospective marks with texts, emails, and phone calls to draw them in.
- Offers that sound too good to be true.
- Pressure to invest right now.
Signs of a Scam
Scammers will:
- Pretend to be someone you trust or from an organization you know
They often pretend to be contacting you on behalf of the government. They may use a real name, like the Social Security Administration, the IRS, Medicare, or make up a name that sounds official. They may also pretend to be from a business you know, like a utility company, tech company, or even a charity asking for donations. - Pressure you and create a sense of urgency
Scammers want you to act before you have time to think. If you’re on the phone, they may tell you not to hang up so you can’t check out their story. - Claim to have a problem or a prize
They might tell you that you’re in trouble with the government, you owe money, someone in your family had an emergency, or there’s a virus on your computer. Perhaps there is a problem with one of your accounts and you need to verify some information. Others will lie and say you won money in a lottery or sweepstakes but must pay a fee to get it. - Tell you to pay in a specific way
They often insist that you pay for something by sending money through a wire transfer, or by putting money on a gift card and sharing the number on the back. Some will send you a check (which will later turn out to be fake), tell you to deposit it, and then send them money.
Identity Theft
Is when someone uses your personal or financial information without your permission.
- Impersonation: A scammer pretends to be someone they are not.
- Online Account Takeover
- Emails and texts can have malicious links and hidden senders which ultimately leads to hacked accounts or a complete online takeover.
- Phone
- Scammers use technology to change the phone number that appears on your Caller ID (or Caller ID Spoofing). The name and number you might see may not be real.
- They can record your voice. If a call has a few moments of silence at first and then you get a “do you hear me?” it could be a scam.
- Robocalls – If you receive a robocall, hang up and don’t press any numbers.
How to Protect Yourself
- Monitor your accounts regularly
- Speak to an associate at your bank
- Make sure you know who you are sending funds to
- Look for the red flags and signs mentioned earlier
- Remember - The bank cannot typically recall a wire - wired funds are gone. You probably won’t get money back!
Email Account Compromise (EAC) and Business Email Compromise (BEC)
EAC is when a personal or corporate email is when an email account is broken into or hacked.
You see a malicious email arrive from a trusted source. It is their actual email address, but someone else has gained access to it, and are utilizing it to send emails on their behalf. It could also be your own account, sending compromised emails on your behalf while you are completely unaware!
BEC involves using deceptive tactics to trick people into making payments to fraudulent accounts. These tactics could be domain spoofing (directing users to a fake site that looks like the real thing), display-name spoofing (using an email display name that looks familiar to the recipient), or lookalike domains (a slightly altered domain name that looks legitimate).
Here’s an example of a lookalike domain: bank@parkbank.com vs bank@parkbnk.com
Tech support scams are also on the rise. Fraudsters pose as customer or tech support from well-known companies, sending pop-ups or messages to resolve fake issues such as a compromised account or a computer virus. The graphic below shows tech support losses over the last 5 years, and how much of an increase there has been since 2017.

The biggest difference between Business Email Compromise (BEC) and Email Account Compromise (EAC):
- BEC = the attacker pretends to be you
- EAC = the attacker IS you
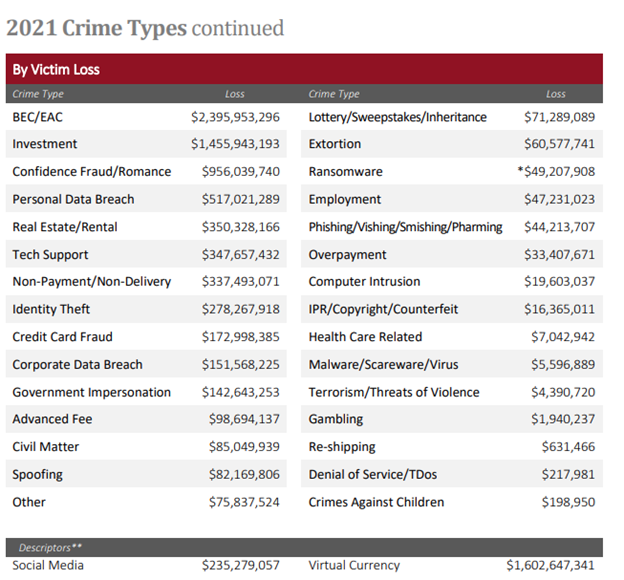
The FBI Internet Crimes Reports below show that BEC/EAC had the highest dollar loss (by victim) in 2021 and that it’s continuing to grow each year.
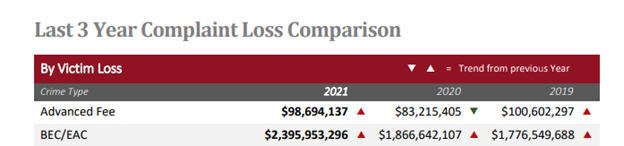
How Does it Happen?
- Password cracking/spraying: An attack utilizing computers to guess your username and password repeatedly until they have access.
- Utilizing information from data breaches to access other accounts. People tend to use the same username(s) and password(s) across various accounts, making it easier for fraudsters to access once they have one set of credentials.
- Keyloggers: A virus that remembers all the keystrokes from your keyboard, then sends it back to an attacker. The attacker then parses the data to try to determine something that may look like a password, a username, and/or a website you may have typed in.
- Once your email account is compromised, attackers will create forwarding rules to send all emails to another account. They will then change passwords on other accounts and go through and delete all sent items – leaving you unaware that there is still fraud happening.
- Insufficient job training
- Phishing/social engineering: You receive a fake email from what you think is a trusted source, you click the link, and you end up typing your username and password into fake web page.
What Can You Do?
- Associate training! Make sure you train your employees to follow proper cyber security guidelines and safely use your accounts and systems while they’re working for your company.
- Use Multi-Factor Authentication (MFA) on everything, not just email.
- Set up email spam filters and make sure they are configured correctly.
- Email encryption involves disguising the contents of email messages to protect potentially sensitive information from being read by someone other than the intended recipients.
- Email sandboxing uses a test environment to determine whether an attachment or link is safe or not, before it delivers it to you.
- Utilize password/passphrase management to store your usernames and passwords in a portal or tool of some sort so you can use different login credentials across various websites. The tool then autofills the credentials or allows you to copy and paste them in a secure manner.
- Email Server Configuration: Mail servers allow the configuration, control, and customization of an organization’s ability to send and receive emails.
- Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) are all protocols that help to protect your domain against spoofing, spamming, and phishing and help to prevent your outgoing messages from being marked as spam.
Identity Protection
Credit Freeze
- Creditors need access to your reporting file. When you apply for a loan or credit card, they’re running a credit check against you. A credit freeze prevents you, or someone else, from running that credit check. If a bad actor tries to sign up for a credit card online using your information, they will be unable to as the creditor will not be able to run that credit check. This is almost a surefire way to prevent someone from opening fraudulent accounts in your name, and has been free to do since 9/21/2018, so there is no cost do you.
- If you know you’re going to purchase a car, or need a loan for something, you can simply open a temporary thaw.
Credit Fraud Alert
- If you suspect identity theft, you can notify the Credit Bureau with a fraud alert. Fraud alerts require creditors to take extra steps to verify identification before opening a line of credit.
Reporting Fraud
If you are a victim…
- Alert your bank!
- Alert the credit bureaus. Contact all the major credit bureaus’ fraud departments. Be sure you have a fraud alert put on your account.
- Report identity theft to the Federal Trade Commission (FTC). Fill out their online complaint form or call 877-438-7338
- File a report with your local police department. It may help you to recover funds if there is a possibility that the fraudsters are caught.
- Get a copy of your credit report. Review the report to see if any credit lines have been opened that weren’t opened by you.
- For a step-by-step guide on how to handle specific identity theft scenarios like tax – related identity theft, misused Social Security Number, medical identity theft, please visit: www.identitytheft.org
Watch the full presentation here:
